Technology
Master 127.0.0.1:62893: Key Guide for Developers & Pros

127.0.0.1:62893: In most CCIE protocol or service, there are several terms or concepts that are sine qua non to anyone in the arena of networking. One such term is “127.0.0.1:62893. “ This combination of numerals and punctuation marks, that can appear utterly arbitrary, is rather crucial within the Information Age , computer science, world wide web , and in internet security. The details and concepts referred to in this article will explain it further in this article number 127.0.0.1:62893, what it implies, the manner in which it is applied, and the context in which it may be employed.
What is 127.0.0.1?
To understand 127.0.0.1:Break down is required when trying to explain the number 62893 in a broader sense, with starting at 127.0.0.1. This is an IP address; it is a basic part of computer networking. Specifically, 127.0.0.1 is normally referred to as the ‘loopback ’ address. This is part of the IPv4 standard and is used to point to the local machine and therefore enable one device to communicate with another.
Loopback Address Explained
The loopback address also known as the embedded IP address is the special address which a computer uses to send messages to itself. This functionality is useful when trouble-shooting and testing network applications and interactions within the network. The following occurs when a packet is sent to 127.0.0.1, it is returned back to the machine that originated them and may never even hit the Internet. This can help developers and the network administrators to ensure that their stack of networks is functioning ok without having to connect to an outside network.
The Role of Ports: Understanding 62893
The second part of the term, 62893, can be identified as a port number. In networking, a port number is a numerical value that refers to a particular process or services running on a computer. Ports enable more than one networked application to run concurrently on a single host since the traffic received is forwarded to the correct service.
Ports and Their Functionality
Ports are divided into three main categories:
- Well-known ports (0-1023): These are reserved for widely-used services and protocols, such as HTTP (port 80) and HTTPS (port 443).
- Registered ports (1024-49151): These are used by software applications to communicate over the network.
- Dynamic or private ports (49152-65535): These are usually assigned dynamically to client applications when they initiate a connection.
Port 62893 falls into the registered or dynamic port range, indicating it is typically used by applications for temporary communication sessions.
127.0.0.1:62893 in Action
Using loopback address (127.0.0.1 ) and adding a port number (62893) generates a distinct handle for a given service executing in the local host. By taking this format it is well named as a socket and is crucial for all network communications.
Practical Applications
1. Web Development and Testing:
Web developers tend to run their applications through the loopback address as a preliminary stage before launching the systems in a live host server. By linking it to the 127 domain, they effectively blacklist their app from running on this computer again .0.0.1: 62893, they can enable it to function properly albeit in a controlled environment.
2. Local Network Services:
Some services and applications are intended to be run locally to minimize the attack surface. For instance, even database, caching servers, and development tools tend to tie to the loopback address to bar outside access.
3. Debugging and Diagnostics:
System administrators or developers commonly utilize the 127.0.0.1: 62893 for debugging purposes. That way, they will be able to do a lot of things which could be interfered with by other services or malicious attacks.
Security Considerations
It is important to note, in this case, that the loopback address and the local ports such as the port 62893 are usually safe from dangers outside of the local machine, but they are not invulnerable. To ensure sufficient protection of localized services, it is necessary to enforce robust security procedures.
Best Practices
1. Access Controls:
Set policy for users and processes to restrict only authorized users to resolve service addresses bound to 127.0.0.1: 62893 . Implement firewall rules and carry out an implementation of Access Control Lists as additional layers of protection.
2. Service Hardening:
The specified program should update software and apply critical patches to counter already-identified risks. ISP is to disable the unnecessary services and features this will gradually reduce the exposure area.
3. Monitoring and Logging:
It is critical to employ comprehensive monitoring and logging to introduce and fight against suspect behaviors. Analyzing logs can provide valuable insights into potential security threats.
Real-World Examples
To illustrate the practical use of 127.0.0.1: 62893, let’s consider a few real-world scenarios:
Example 1: Local Web Server Development
The use case scenario can be created having a web developer that is in the process of developing a new application with the need to test it locally before deploying it on the World Wide Web. They set the web server to start listening at 127.0.0.1: 62893 This setup allows the developer to access the application in a web browser by navigating to 127.0.0.1: 62893. Since the application is bound to the loopback address, it is accessible only from the local machine, ensuring a secure testing environment.
Example 2: Database Access for Development
A software engineer is developing a new feature that requires interaction with a database. To avoid impacting the production database, they set up a local instance of the database server bound to 127.0.0.1 :62893. The application connects to this local instance for development and testing, ensuring that any changes do not affect live data.
Example 3: Debugging Network Services
The given situation is imagined as the current work of a network administrator that has a problem with a local network service. They coordinate the waiting service with the numerical IP address of exactly 127, in numerous locations throughout the full text.0.0.1:62893 to fully disconnect it from other parts of the network as if it were not even connected. This kind of setting makes it easier for the administrator to perform service isolation to diagnose and fix issues without outside network intervention.
Conclusion
Understanding 127.0.0.1:62893 is useful for anybody that is in networking, web designing or web development and more importantly in securing networks and data. Apparently, the incorporation of this loopback address along with the port number creates a tight foundation for the local test, development, and protection of services. Adhering to these procedures in gaining Computing Administrators can fully leverage the use of 127.0.0.1: 62893 Its overall value maintains good interaction with the requirements of users together with guarding them from any threats that may possibly infiltrate its network.
Because the technology environment is evolving, we were unfortunate enough not to forget about such basic yet indispensable ideas as 127.0.0.1: 62893 is invaluable. The knowledge of how to work with the loopback address and ports is vital for everybody who is going to create a new application, who faces difficulties with a network service, or who tries to implement a security feature on the local network level. Applying this knowledge contributes to enhancement in technical knowledge and will enhance integrity and safety of networked systems.
Technology
Free Cent Slot Machine Online: An Enjoyable and Affordable Method to Play Ports
If you appreciate playing slots however do not wish to invest a lot of money, cost-free cent ports online can be an excellent choice. These games allow you to experience the excitement of spinning betine güncel giriş the reels without damaging the bank. In this article, we’ll explore how you can play totally (more…)
Technology
Free Slot Machines: The Ultimate Overview
Slots have actually long been a preferred type of enjoyment for casino players around the globe. With the improvement of innovation, on the internet vending machine have gotten tremendous appeal, allowing gamers to appreciate the adventure of spinning the reels from the convenience of their own homes. While lots of players are attracted to the enjoyment (more…)
Technology
Free Video Game Casino Site: An Overview to Online Casino Site Gamings
Are you a fan of online casino games yet do not want to spend any cash? Look no more! Free game casino sites provide a vast array of on-line gambling enterprise games that you can play without investing a solitary dime. Whether you’re a newbie or a seasoned player, these cost-free video games provide a superb chance to enhance your skills, experiment (more…)
-

 Health11 months ago
Health11 months agoDiscover ://vital-mag.net Blog: Expert Tips for Total Wellness
-
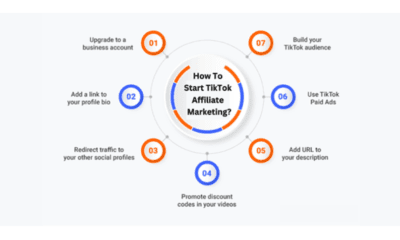
 Business12 months ago
Business12 months agoTikTok Affiliate Marketing | A Complete Guide for Marketers and Creators |
-
 entertainment5 months ago
entertainment5 months agoTop 7 Occasions to Send a Thank You Card and Why They Matter
-

 Health11 months ago
Health11 months ago7 Day Juice Fast Weight Loss Results: Expectations & Strategies
-

 entertainment5 months ago
entertainment5 months agoCelebrate Life: The Pleasure in Sending Birthday Cards
-

 Home and Gardening11 months ago
Home and Gardening11 months agoSunset Gardens Apartments: Complete Guide
-

 Life style12 months ago
Life style12 months agoWhy i stopped eyelash extensions?
-

 Business12 months ago
Business12 months agoSecret Strategies of Competent Trading Companies
